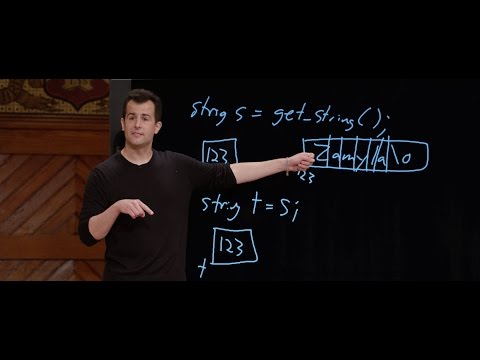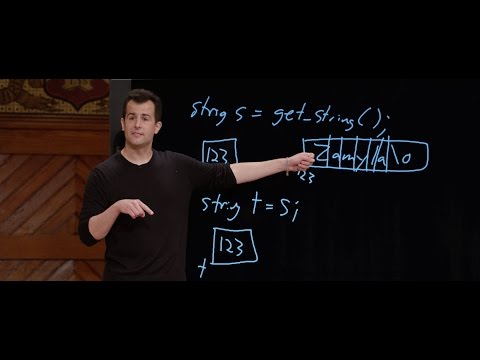CS50 2016 - 第4週 - 記憶 (CS50 2016 - Week 4 - Memory)
Amy.Lin が 2021 年 01 月 14 日 に投稿  この条件に一致する単語はありません
この条件に一致する単語はありません- n. (c./u.)模範 : 見本;模様 : 柄;様式;規則性;型紙
- v.t.模倣する;模様をつける
US /ˈkærəktɚ/
・
UK /'kærəktə(r)/
- n.(物語 : 映画 : 演劇などの)登場人物;文字;性格 : 性質;変わっている人;評判
エネルギーを使用
すべての単語を解除
発音・解説・フィルター機能を解除